
NBOBE - HS Dhllan Horel Hight highlights the future explained in Vegas. The NBA summer division is officially here and is the annual tradition of watching the most important result of basketball on TV.Not really does it matter (except your...

The rules based globally are in retreat and violence is increasing, which has consumed countries to review their relations. Within a week, his former companions distinguished the 80th anniversary of the celebration of the Second Second Wind, the feeling of...
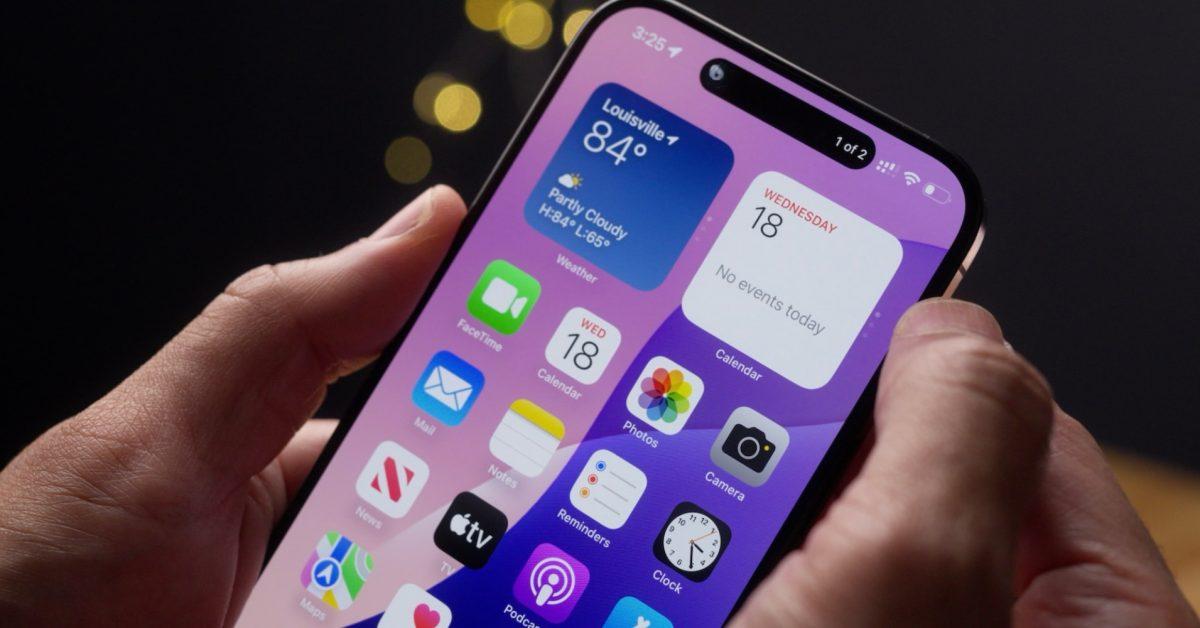
In a variety of rumors about the dynamic island of the iPhone 17 line, liqueur has followed major changes for the facility. There are rumors in all the dynamic islands of iPhone 17, some reliable resources with some reliable resources...

Bad bunny has launched to become 30 who never occurred before the Cotiso de Puerto Rico with MasterClass Arigi in normal in normal in normal At this point it makes you feel undeniable: the first half of the decade belonged...

Tahaad petiford auburn tigers were arrested for alcohol management in Lee, Alabama. Auburn Tigers Star Tahaad Pettiford was arrested at the filling of DUI in Alabama;The coach reacts Auburn Tigers was arrested for driving alcohol in the state, Alabama. The...

Robert Macintyre could not call his second round nothing but "absolutely scary" though he could only break the smile that would be close Robert Macintyre battles for homework, Colin Morikava makes great names in Genesis in Scottish Open Reading 2...

Studies show that the AI-powered data analysis can improve power equipment Apple's next Apple Watch upgrade, how often we can upgrade to our understanding? Research shows that AI-driven data analysis improves the current juggling hardware Apple presents one of the...

Remember the times when our grandmas used to clip coupons from newspapers and magazines to score a deal on the weekly groceries? With the arrival of platforms like Cuponation, the art of saving has entered the digital age.

This is your first post. Stay tuned for amazing updates in Sports, Technology, Health and more!